Date: 09/02/2022
Threat actor target Ubiquiti network appliances using Log4Shell exploits

Threat actor target Ubiquiti network appliances using Log4Shell exploits – The Record by Recorded Future Threat actors are using a customised public exploit for the Log4Shell vulnerability to attack and take over Ubiquiti network appliances running the UniFi software, security firm Morphisec said in a report last week. The attackers used a proof-of-concept exploit previously […]
Read more
Date: 07/02/2022
Deadbolt Ransomware Hits More Than 3,600 QNAP NAS Devices

Deadbolt ransomware hits more than 3,600 QNAP NAS devices – The Record by Recorded Future More than 3,600 network-attached storage (NAS) devices from Taiwanese company QNAP have been infected and had their data encrypted by a new strain of ransomware named Deadbolt. According to a copy of the ransom note, device owners are told to […]
Read more
Date: 20/01/2022
How Microsoft Aligns and Matures Essential 8 Mitigation Strategies

The Essential Eight are a baseline set of security controls that been recommended by The Australian Cyber Security Centre to help mitigate malicious cyber activity for organisations. To help with the implementation of these controls, the Australian Signals Directorate (ASD) has defined an Essential Eight maturity model, detailing the different levels of maturity to help […]
Read more
Date: 11/01/2022
What is the Essential 8 and Why Should You be Interested?
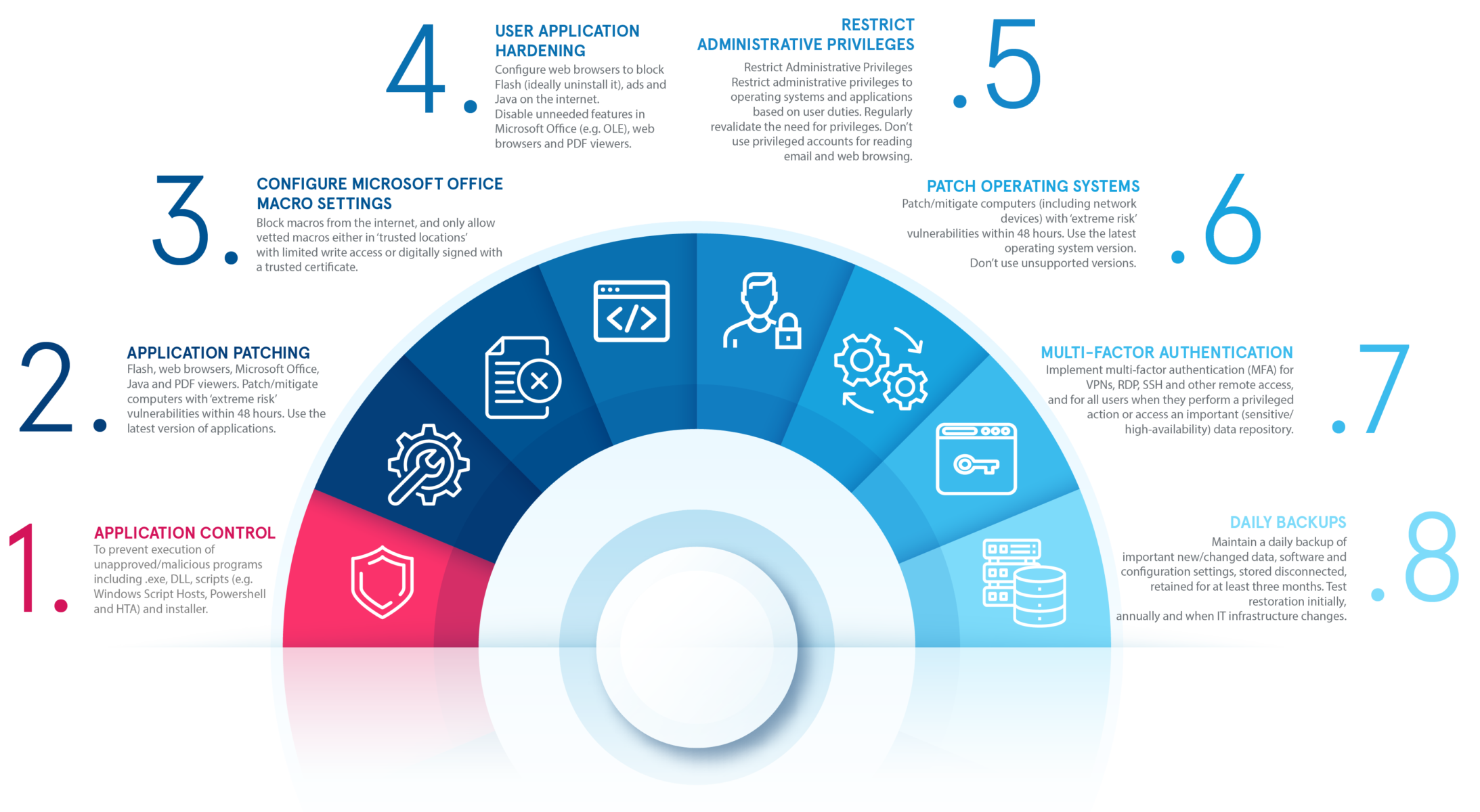
What is the Essential 8? The Essential Eight is a baseline set of mitigation strategies that have been developed by the Australian Cyber Security Centre (ACSC). These mitigation strategies have been developed by the ACSC to help organisations protect themselves against various cyber threats regardless of their industry. 1. Application Control 2. Application Patching 3. […]
Read more
Date: 22/12/2021
30% Rise In Ransomware Attacks Over Holiday Season

Report reveals 30% rise in ransomware attacks during the holidays – Cyber Security Connect Darktrace has reported that its security researchers discovered a 30% increase in the average number of attempted ransomware attacks globally over the holiday season in every consecutive year from 2018 to 2020 compared, with the monthly average. According to Justin Fier, […]
Read more
Date: 14/12/2021
SA Government Hit By Cyber Attack

SA government hit by cyber attack – Cyber Security Connect South Australian Premier Steven Marshall is among 38,000-80,000 employees with personal information exposed as a result of a ransomware attack on external payroll software provider Frontier Software. According to the SA government, the personal information includes names, dates of birth, tax file numbers, home addresses, bank account details, remuneration and superannuation contributions. The breach is currently under investigation, with the government offering support to affected employees. As organisations become more reliant on SaaS products, it’s crucial when making purchasing decisions to consider potential SaaS providers’ security posture and practices, as it can and will have direct impacts on their customers when they suffer outages due to cyber incidents. Attackers are increasingly using an organisation’s supply chain partners to gain access to confidential and sensitive information, particularly if they identify a weak link. As such, it’s imperative organisations are working closely with their supply chains to understand the security of businesses they collaborate with and work together to address vulnerabilities. For over ten years, Acurus has been trusted by Australia’s largest household brands, including Energy Australia, Officeworks, Bakers Delight, […]
Read more

















